Os perigos ocultos do cibercrime os riscos apresentados por hackers operando nas sombras ia generativa | Foto Premium

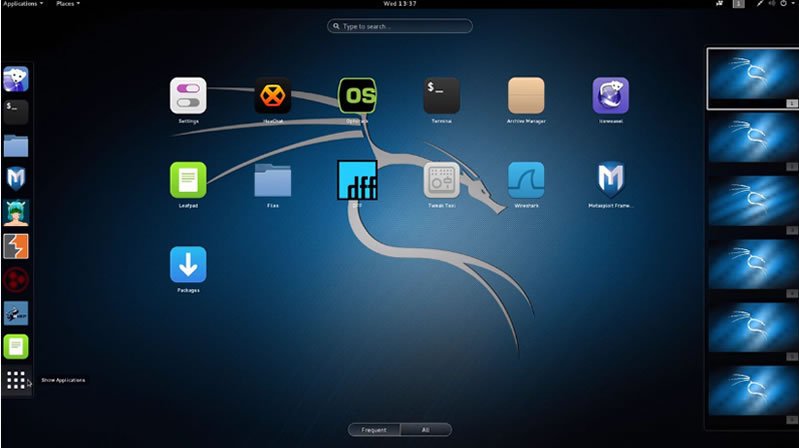
Cybersecurity Prism - Why Do Hackers Use Kali Linux OS? A hacker is fundamentally someone who breaks into computer networks or standalone personal computer systems for the challenge of it or since